By disabling the ability for users in your Office tenant to consent to apps (best security practice) you may run into an issue when your first Apple iPhone user tries to access their work emails similar to the image below –
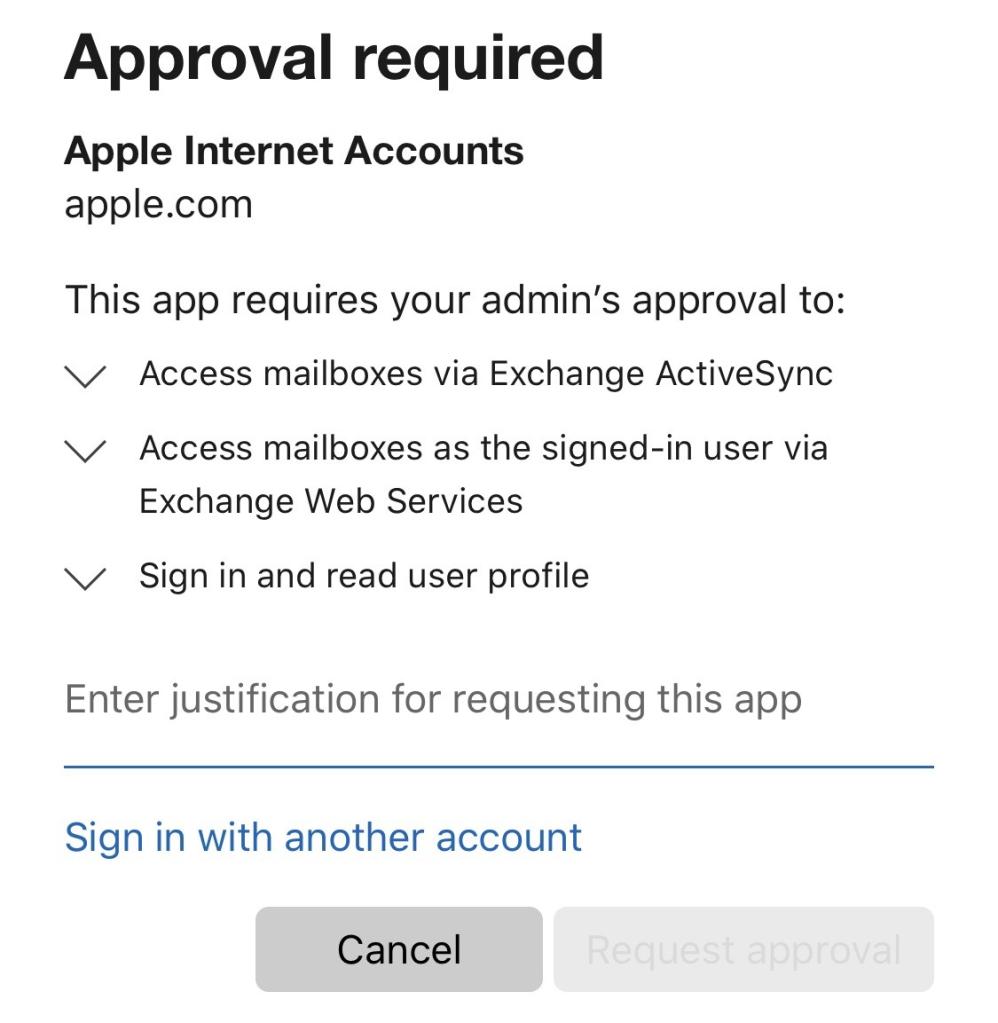
So there’s two ways around this, you can either –
- Allow your users to consent to apps which although not ideal is a valid option – Managing user consent to apps in Microsoft 365
- Authorise the application on the users behalf.
In this article I’ll cover how to quickly authorise the application, before that though I’d like to explain why opening up the ability to consent to apps to any user is a bad idea – What is the illicit consent grant attack in Office 365?
Authorise the App
- Get your tenant ID.
- Navigate to portal.azure.com
- Select ‘Azure Active Directory’
- In the Overview panel, copy the Tenant ID shown in the Tenant information box as shown below –

- Navigate to the Apple Accounts consent screen, to do this navigate to the URL below, replacing the <tenantID> portion with your tenant ID from the previous step and the <redirectURI> with a valid URL (this can be anything really EG. https://microsoft.com).
https://login.microsoftonline.com/<tenantID>/oauth2/authorize?client_id=f8d98a96-0999-43f5-8af3-69971c7bb423&response_type=code&redirect_uri=<redirectURI>&prompt=admin_consent
- Once the Permission requested dialog window appears, click Accept to approve the app.
- Now your users should be able to access the mail app via Apple devices.

communities
LikeLike
IB
LikeLike
Robust
LikeLike
Analyst
LikeLike
Internal
LikeLike
Tenge
LikeLike
Do you find any specific concern about this Apps? We are evaluating OAuth policy and there are different opinion about this topic.
LikeLike